Date: 2021feb26
Q. Wireguard: Fedora server and Android client
A. This article in Fedora Magazine
https://fedoramagazine.org/build-a-virtual-private-network-with-wireguard
was my starting point. However I changed some things.
Fedora Server
Install
dnf install wireguard-tools
Make config folder
mkdir /etc/wireguard
cd /etc/wireguard
umask 077
Make keys
wg genkey | tee privatekey | wg pubkey > publickey
Make the server config file /etc/wireguard/wg0.conf
[Interface]
Address = 192.168.2.1/24
PrivateKey = <SERVER-PRIVATE-KEY>
# PostUp = Not necessary
# PostDown = Not necessary
ListenPort = 51820
[Peer]
# My phone
PublicKey = <PHONE-PUBLIC-KEY>
AllowedIPs = 192.168.2.3/32
The 192.168.2.x range is for examples - changed it to something else
Ensure you have forwarding enabled in /etc/sysctl.conf
net.ipv4.ip_forward=1
net.ipv6.conf.all.forwarding=1
If you needed to change that file do:
sysctl -p
I made a file called /etc/firewalld/services/mywireguard.xml with a custom port:
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>Wireguard VPN</short>
<description>Wireguard VPN</description>
<port protocol="udp" port="51820"/>
</service>
And added a reference to /etc/firewalld/zones/FedoraServer.xml
<?xml version="1.0" encoding="utf-8"?>
<zone target="default">
<short>Public</short>
...
<service name="mywireguard"/>
<masquerade/>
</zone>
Then reload
firewall-cmd --reload
Now we can start the server
systemctl start wg-quick@wg0
Android client
Here is how I setup a client on Android
The interface
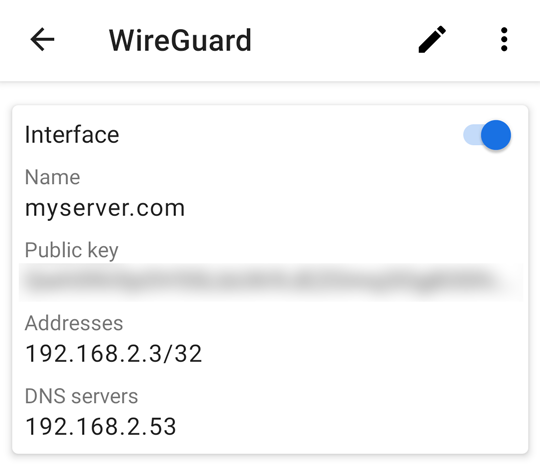
This assigns the Android phone as address 192.168.2.3
It tells it to use the DNS server at 192.168.2.53 which is
the DNS server on my LAN.
The peer (ie the server)
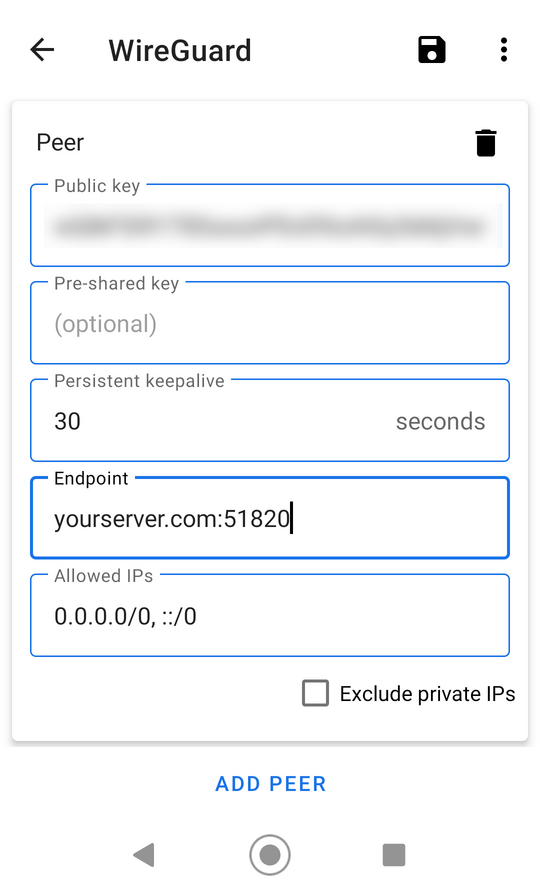
The entry in Allowed IPs says we want Wireguard for all IP-addresses
If you're on a paid link you may want to turn off the keep alive.
Testing
Use termux on Android to
ping google.com
On the Fedora side
wg
Will show
interface: wg0
public key: <PUBLIC-KEY>
private key: (hidden)
listening port: 51000
peer: <PUBLIC-KEY>
endpoint: <IP-ADDRESS>:41984
allowed ips: 192.168.2.3/32
latest handshake: 39 seconds ago
transfer: 4.62 MiB received, 71.96 MiB sent
So you can see if its handshaked and how much has been transferred
Dump all Wireguard traffic
tcpdump -n -v -i wg0
I made a TUI application that helpfully runs all these applications in one Window
https://github.com/dmdmdm/wireguard-monitor
 This assigns the Android phone as address 192.168.2.3
It tells it to use the DNS server at 192.168.2.53 which is
the DNS server on my LAN.
The peer (ie the server)
This assigns the Android phone as address 192.168.2.3
It tells it to use the DNS server at 192.168.2.53 which is
the DNS server on my LAN.
The peer (ie the server)
 The entry in Allowed IPs says we want Wireguard for all IP-addresses
If you're on a paid link you may want to turn off the keep alive.
Testing
Use termux on Android to
The entry in Allowed IPs says we want Wireguard for all IP-addresses
If you're on a paid link you may want to turn off the keep alive.
Testing
Use termux on Android to